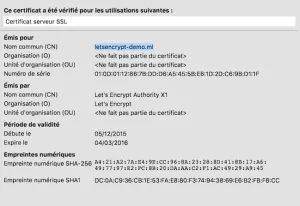
Let's encrypt is now in public beta!
Kevin Raynel4 min read

To celebrate this, I will guide you through the 6 steps required to get an auto-hosted, HTTPS website. With its own TLD domain. For free. Yeah!
It should take a few minutes of your time. We will only be using free services. It will also allow you to try the https://letsencrypt.org initiative on an Nginx server.
Step 1:
There are some services that allow you to register domains for free:
Unfortunately, it will not work with these domains. Let’s encrypt is currently limiting the number of certificates issued per top domain (*.noip.me, *.cu.cc…), and you will most likely not be the first one on these domains.
The solution I found is to use http://freenom.com which offer free TLDs (.ga, .ml…): it works, but I would only use it for personal use.
Choose your domain name, and enter your DNS records.
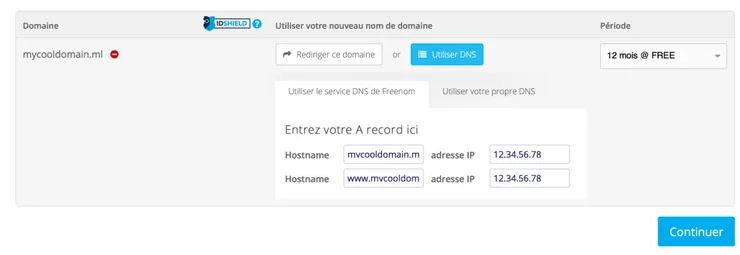
Step 2:
I will assume for all the following commands that you are using a Debian based distribution, but you can easily find documentation for your favorite distro.
Boot up your Raspberry pi or whatever server you will be using to host your website, SSH to it, and install Nginx:
user@webserver:~$ sudo apt-get update && sudo apt-get upgrade
user@webserver:~$ sudo apt-get install nginx
user@webserver:~$ sudo /etc/init.d/nginx start
Test the default, local website: http://my.rpi.local.ip
If you do not know Nginx or want to know more, Maxime wrote a nice article about the basics of nginx.
Step 3 (optional):
Write a website. Easiest step ever.

Or you can just use the default website, nobody is judging you…
Step 4:
Edit the nginx configuration file for your website.
user@webserver:~$ sudo vim /etc/nginx/sites-available/default
Listen on the server name you registered earlier: server_name myhostname.ga
Save, restart nginx: sudo /etc/init.d/nginx restart
Step 5:
In your router, add a static route for your server, open ports 80 and 443 and redirect them to your internal ip.
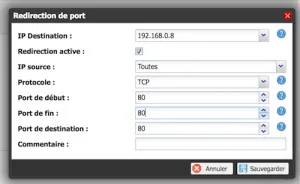
Try the HTTP website on the public domain you registered earlier:
http://myhostname.go. If you get an answer, you are good to go. If not, wait longer for the DNS redirection to propagate.
Step 6: Let the magic begin!

First, install the letsencrypt cli on your webserver.
user@webserver:~$ git clone https://github.com/letsencrypt/letsencrypt
user@webserver:~$ cd letsencrypt
Enabling Nginx plugin
As Nginx is not yet supported, you have to enable it manually. If you use Apache, this step is not required.
user@webserver:~/letsencrypt$ vim bootstrap/venv.sh
Find line
$VENV_BIN/pip install -U -r py26reqs.txt letsencrypt letsencrypt-apache # letsencrypt-nginx
and uncomment letsencrypt-nginx. It becomes:
$VENV_BIN/pip install -U -r py26reqs.txt letsencrypt letsencrypt-apache letsencrpyt-nginx
Generate first certificate!
You are now ready to obtain your first Let’s encrypt certificate. We will use the default command, with the debug, verboseand nginx flags enabled:
user@webserver:~/letsencrypt$ ./letsencrypt-auto --nginx --debug --verbose
And just follow the wizard…
Result
Go visit your website again, only this time, hit the https endpoint.
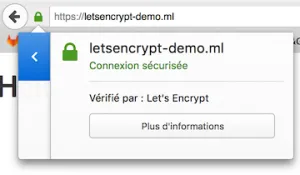
(Very light) Troubleshooting

If you have an error when signing your certificate request:
Error: urn:acme:error:rateLimited:: There were too many requests of a given type:: Error creating new cert:: Too many certificates already issued for: noip.me/cu.cc/…
you probably missed the line in step 1:
Unfortunately, it will not work with these domains.
Buy a domain or find another one!
Conclusion
Let’s encrypt is in very early development phase for nginx, and not really supported at the moment. The script updates /var/nginx/nginx.conf with the required configuration. Still, you can access the generated keys and certificates:
/etc/letsencrypt/live/<domain name>/privkey.pem/etc/letsencrypt/live/<domain name>/fullchain.pem
You are obviously free to use these certificates any way you want and edit the nginx configuration files. However, these certificates are only valid for 3 months. The main idea behind Let’s encrypt is to automate the generation of certificates.
The automation step seems ready for Apache (you add a cronjob calling letsencrypt-auto and that’s it, your certificates get updated), but not quite yet for Nginx. If you want to use the automatic renewal, you probably will have to keep the configuration files untouched.
However, a number of projects are starting to appear. For instance, a Docker Let’s Encrypt companion container for nginx-proxy was shared some days ago by the docker team, or Synology announced they will soon integrate Let’s Encrypt in the DiskStation Manager.